Employee monitoring with behavior and data insights analytics!
Behavioral Analytics, Data Insights & Enforcement for All Organizations
 |
Inside Threat PreventionProtect sensitive and confidential company data from loss caused by accidental, negligent or compromised insiders with insider threat prevention fueled by data-driven endpoint monitoring
|
 |
Business Process OptimizationReimagine how business gets done with business process optimization data that creates more efficient systems, increase productivity and streamline processes.
|
 < < |
Employee MonitoringGo beyond basic employee monitoring with data-backed behavior analytics that provide actionable insights for productivity, data security and compliance while maintaining employee privacy.
|
 < < |
ForensicsStrengthen data loss prevention with a robust endpoint monitoring system that identifies and blocks malicious user activity.
|
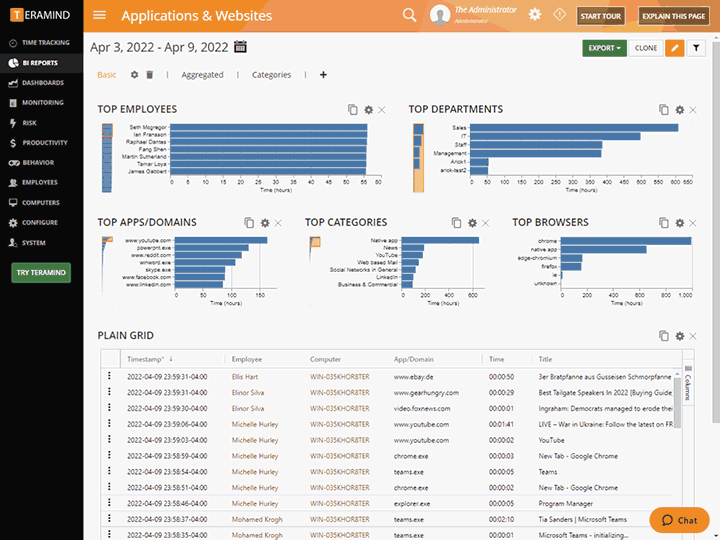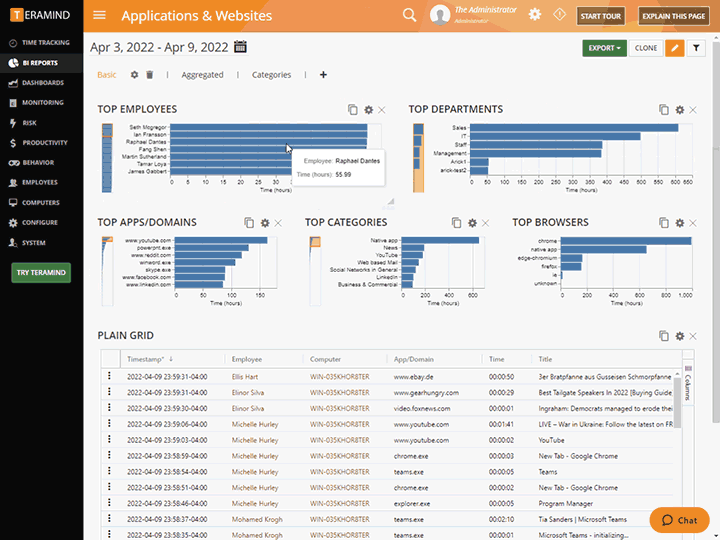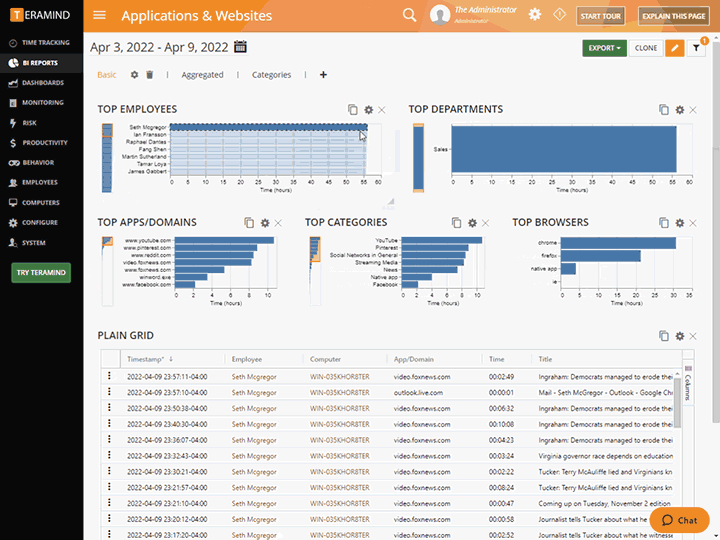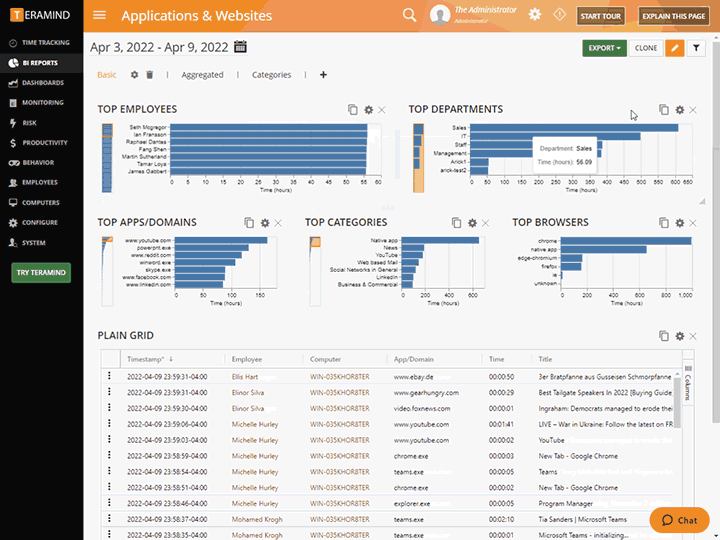 < < |
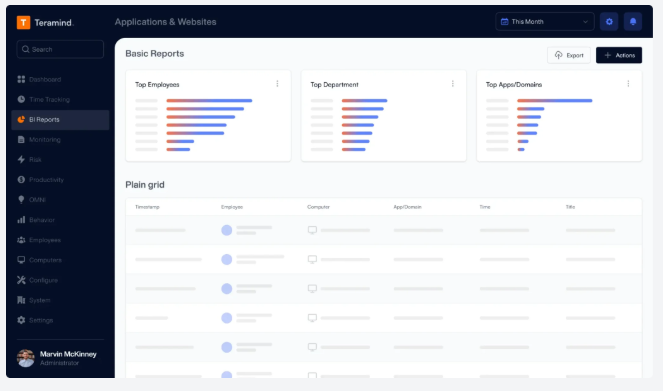
Business Intelligence ReportsView key activity data and multi-level reporting in Teramind’s intuitive Business Intelligence Dashboard that simplifies complex data and analysis, and presents them as easy-to-read charts, graphs and maps. |
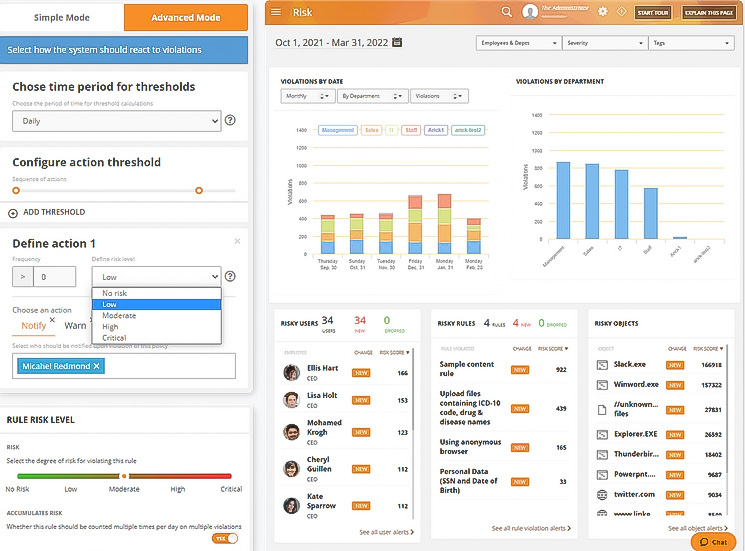
Inside Threat Prevention
Protect sensitive and confidential company data from loss caused by accidental, negligent or compromised insiders with insider threat prevention fueled by data-driven endpoint monitoring
- Time-Stamp Screen Recording
- Smart Rules For High-Risk Users
- Website & Application Monitoring
- Keystroke Logging
Business Process Optimization
Reimagine how business gets done with business process optimization data that creates more efficient systems, increase productivity and streamline processes.
- In-app Field Parsing
- Website & Application Monitoring
- Screen recording with Historical Playback
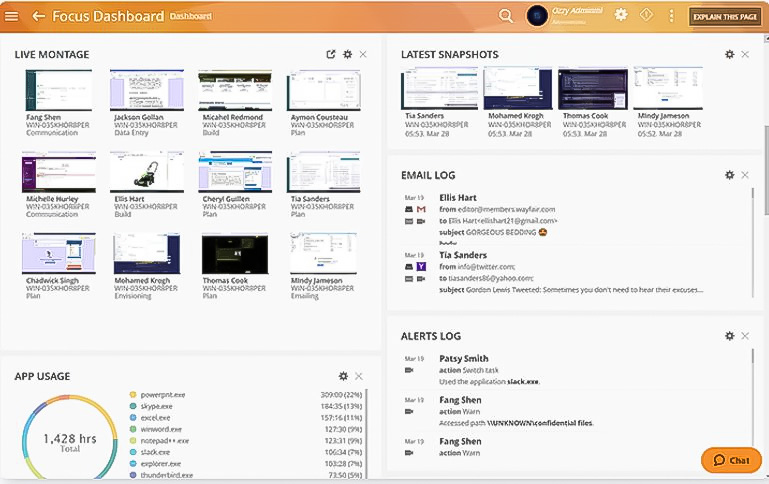
Employee Monitoring
Go beyond basic employee monitoring with data-backed behavior analytics that provide actionable insights for productivity, data security and compliance while maintaining employee privacy.
- Performance Analytics
- Who’s Working, and Who’s Not
- Monitor What Matters, Not What Doesn’t
- Measure Teams Goals Against KPI’s

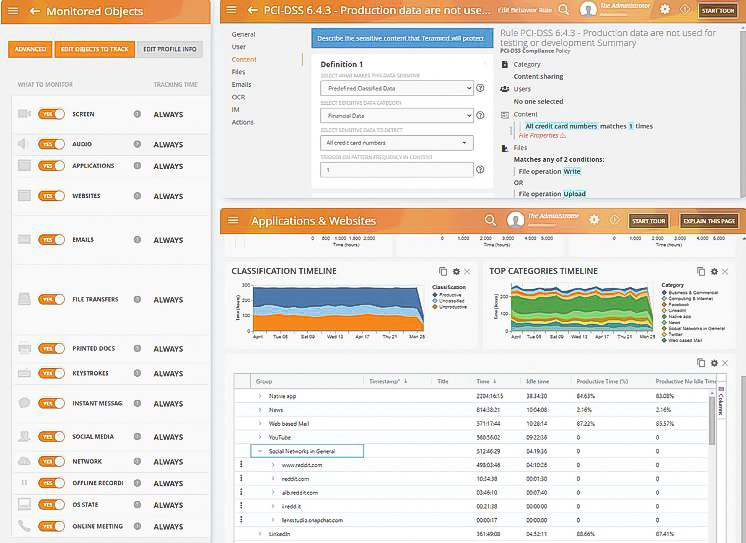
Forensics
Strengthen data loss prevention with a robust endpoint monitoring system that identifies and blocks malicious user activity.
- Interpret Data and Trends
- Uncover Pods of Internal Toxicity
- Identify Early Signs of Threats
- Detect Worker Activity Falsification
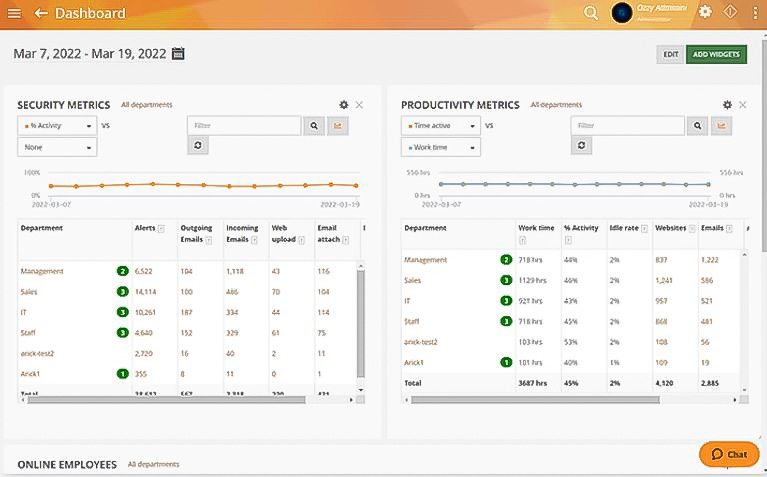
Business Intelligence Reports
View key activity data and multi-level reporting in Teramind’s intuitive Business Intelligence Dashboard that simplifies complex data and analysis, and presents them as easy-to-read charts, graphs and maps.
Hidden Productivity Blockers? We Bring Them to Light.
Our employee tracking software seamlessly integrates with your current systems to provide actionable insights that boost both productivity and security.
 |
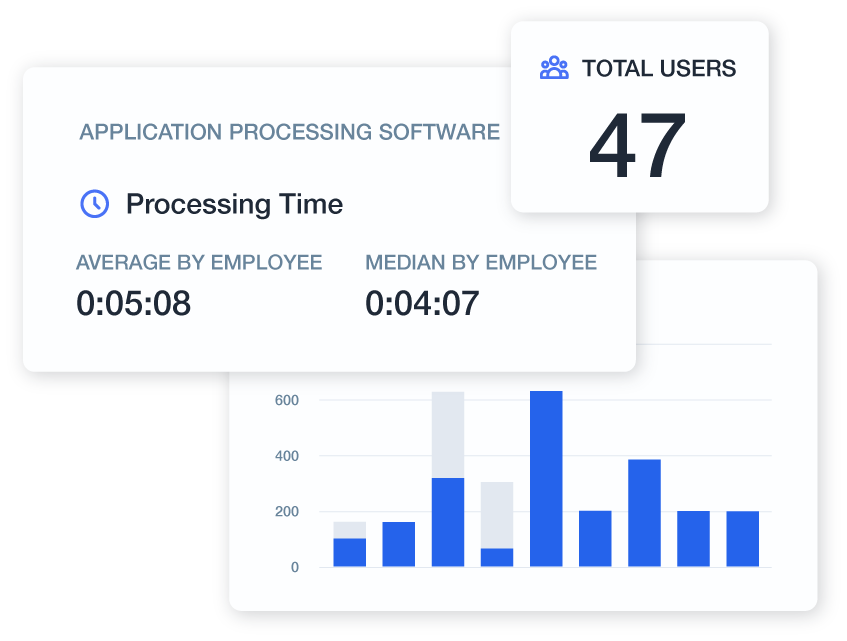
Activity MonitoringGain deep insights into employee workflows with advanced user activity tracking tools.
|
 |
Privacy-Focused MonitoringEnsure effective oversight while maintaining employee trust with responsible, transparent monitoring practices.
|
 |
Website and Application TrackingUnderstand how employees interact with digital tools to optimize productivity and policy compliance.
|
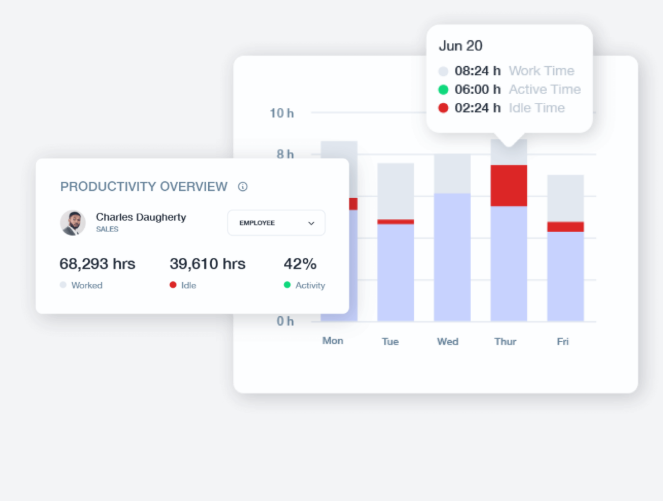 |
Productivity Analysis and OptimizationConvert employee activity data into meaningful insights that enhance performance and operational efficiency.
|
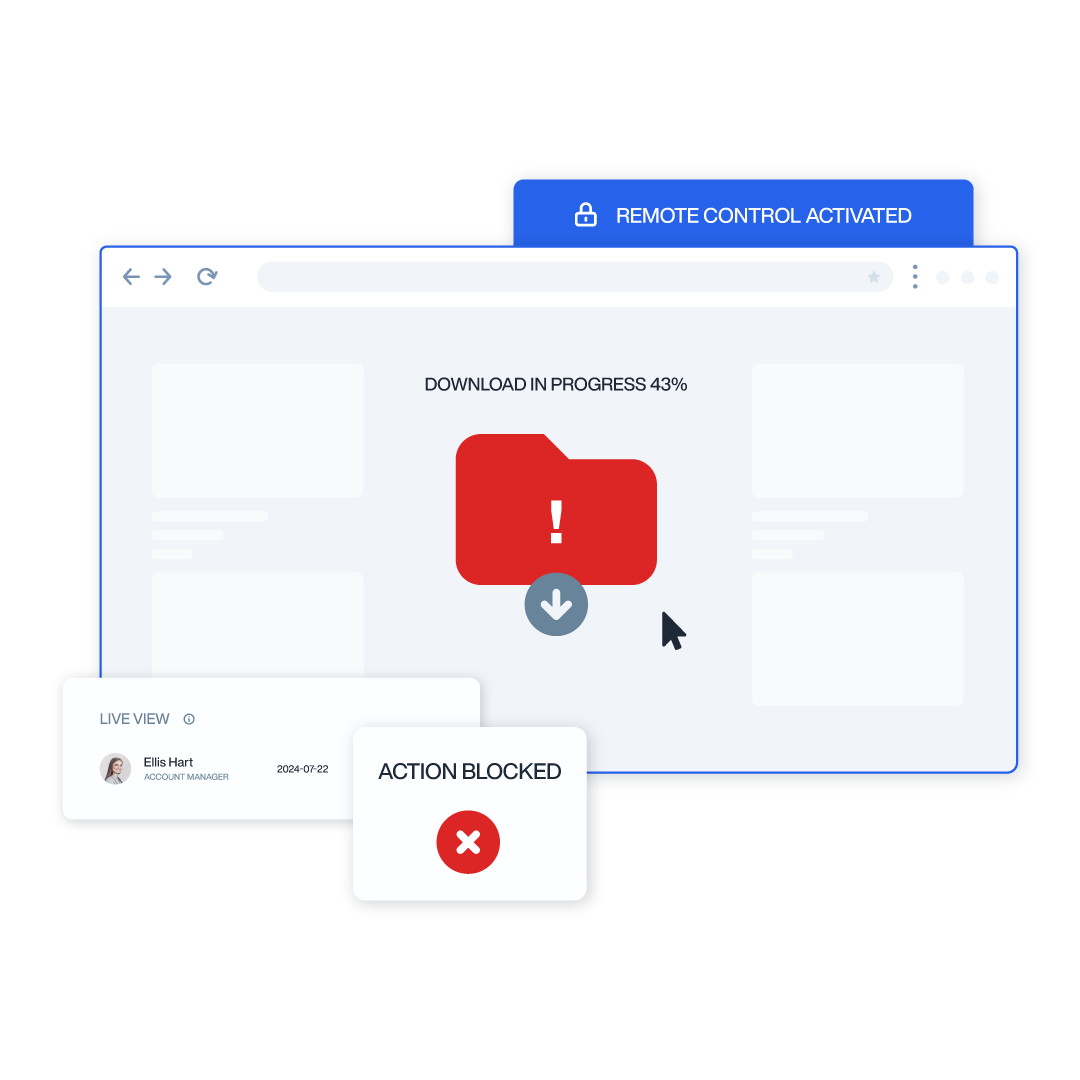 |
Insider Threat DetectionSafeguard critical data by identifying and responding to both accidental and malicious insider risks.
|
 |
Customizable ReportingEmpower stakeholders with tailored reports and visual dashboards that translate activity data into strategic insights.
|
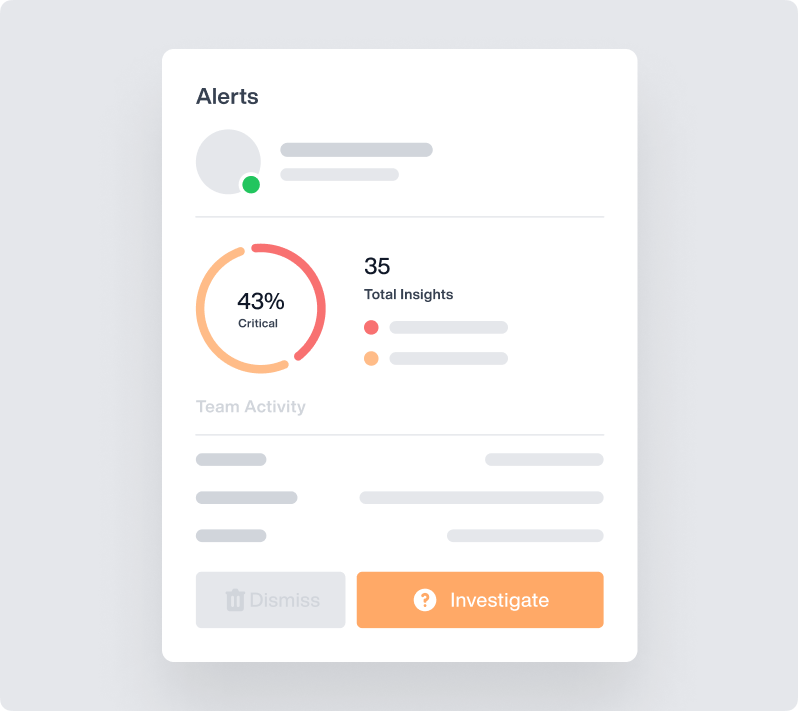 |
OMNI: AI-Powered AlertsOMNI is Teramind’s intelligent alert interface, designed to surface what matters most—fast.
|
Activity Monitoring
Gain deep insights into employee workflows with advanced user activity tracking tools.
- Screen Monitoring: Capture continuous or event-based screenshots that offer context into user actions while optimizing storage.
- Application Usage: Track app usage duration, detect unauthorized software, and mitigate potential security threats.
- Keystroke Logging: Monitor keystrokes in sensitive applications to prevent data leaks and enhance security controls.
Privacy-Focused Monitoring
Ensure effective oversight while maintaining employee trust with responsible, transparent monitoring practices.
- Clear Policies: Establish and communicate monitoring guidelines that foster trust with remote staff and freelancers.
- Targeted Monitoring: Focus solely on work-related activities during business hours, avoiding unnecessary intrusion.
- Minimal Data Collection: Teramind gathers only essential data with defined retention periods, balancing privacy with operational needs.
Website and Application Tracking
Understand how employees interact with digital tools to optimize productivity and policy compliance.
- URL Filtering: Manage website and social media access with customizable rules that align with your organization’s productivity goals.
- Content Analysis: Analyze visited web content to detect potential policy breaches—while maintaining employee privacy.
- Time Distribution: Track how time is allocated across productive and non-productive apps, with insights by individual and department.
Productivity Analysis and Optimization
Convert employee activity data into meaningful insights that enhance performance and operational efficiency.
- Work Patterns: Uncover peak productivity times and signs of burnout by analyzing daily and weekly activity trends.
- Project Integration: Sync with tools like Jira, Zendesk, and Redmine to track effort accurately and improve resource allocation across distributed teams.
- Idle Time Insights: Differentiate between necessary breaks and unproductive downtime to encourage balance while addressing performance gaps.
Insider Threat Detection
Safeguard critical data by identifying and responding to both accidental and malicious insider risks.
- Behavioral Anomaly Detection: Set behavior baselines and get alerted to unusual actions that may signal a potential threat.
- Data Loss Prevention: Monitor file movements, email attachments, and clipboard usage to block unauthorized data transfers.
- Access Control Monitoring: Ensure users access only what they’re permitted to, and flag suspicious privilege escalation attempts.
Customizable Reporting
Empower stakeholders with tailored reports and visual dashboards that translate activity data into strategic insights.
- Executive Dashboards: Present leadership with clear, visual summaries of productivity trends, risk alerts, and compliance metrics.
- Team Performance Analysis: Compare departmental performance to uncover strengths, share best practices, and drive improvement.
- Regulatory Compliance: Create comprehensive activity logs that meet compliance standards and demonstrate responsible monitoring.
OMNI: AI-Powered Alerts
OMNI is Teramind’s intelligent alert interface, designed to surface what matters most—fast.
- View AI-curated alerts in a streamlined news feed, highlighting key trends and potential risks.
- Drill down into details directly from your dashboard to take swift, informed action and stay ahead of emerging threats.
The Features That Power Teramind
Live View & Historical Playback
Optical Character Recognition
Website Monitoring
Application Monitoring
Email Monitoring
Instant Message Monitoring
Social Media Monitoring
Network Monitoring
Citrix Monitoring
Remote Desktop Control
RDP Session Recording
Productivity Analysis
Active Vs. Idle Time Logs
Unproductive Work Time Analysis
Compare benefits


